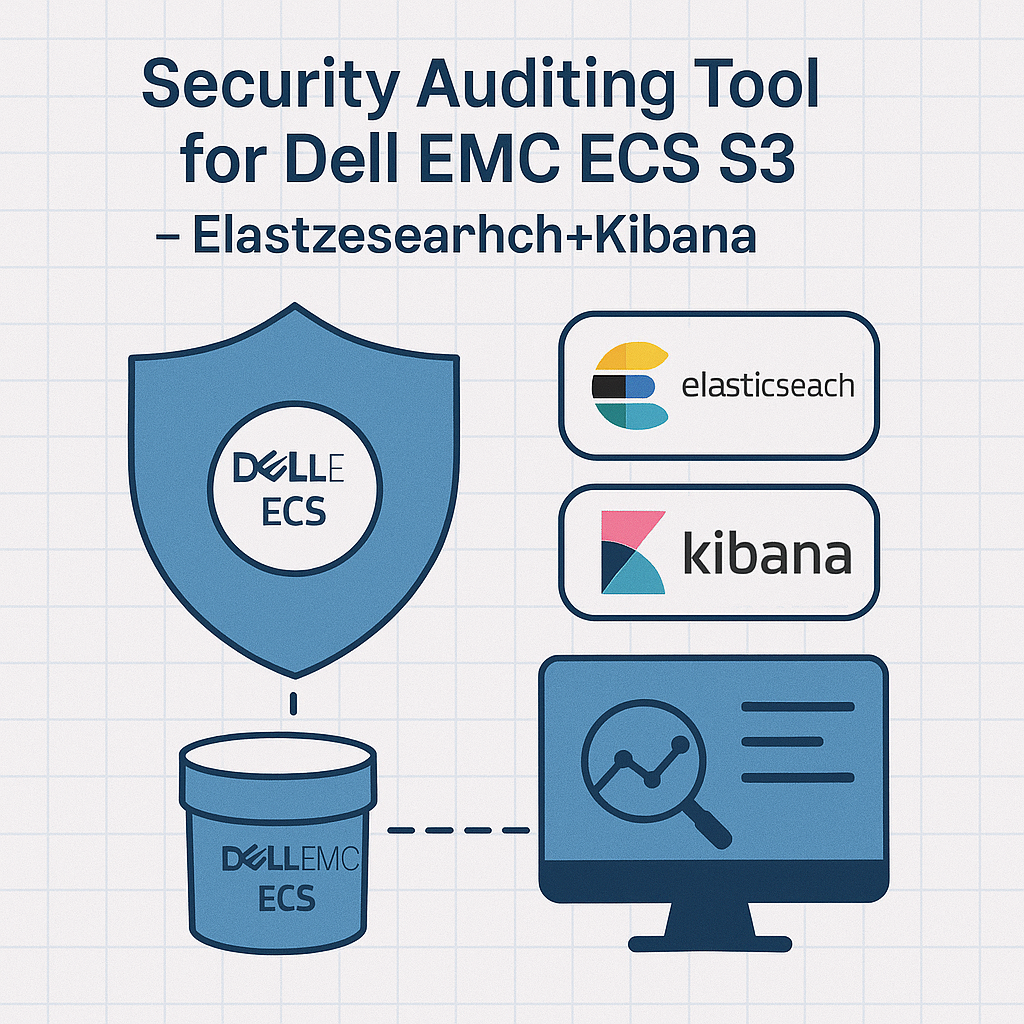
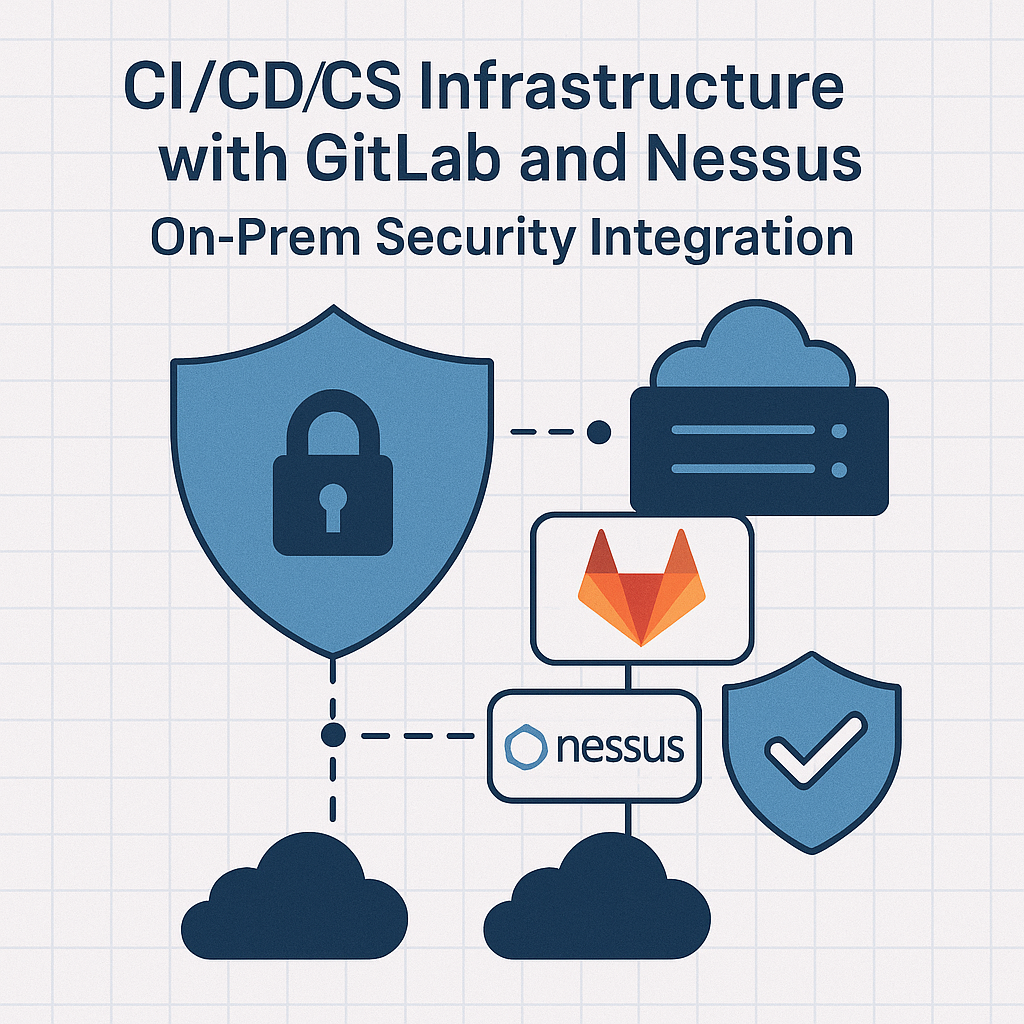
AWX building custom execution environment
AWX default execution environment is pretty strong but in some cases it is not enough. There days I wanted to run a play which require json_query for filtering out some outputs. All went well during tests from localhost so when I’ve wanted to run it using AWX I’ve got a super nice error: Well this was the time when I saw a miss in default AWX EE and something challenged me to fix it. First...
Read more