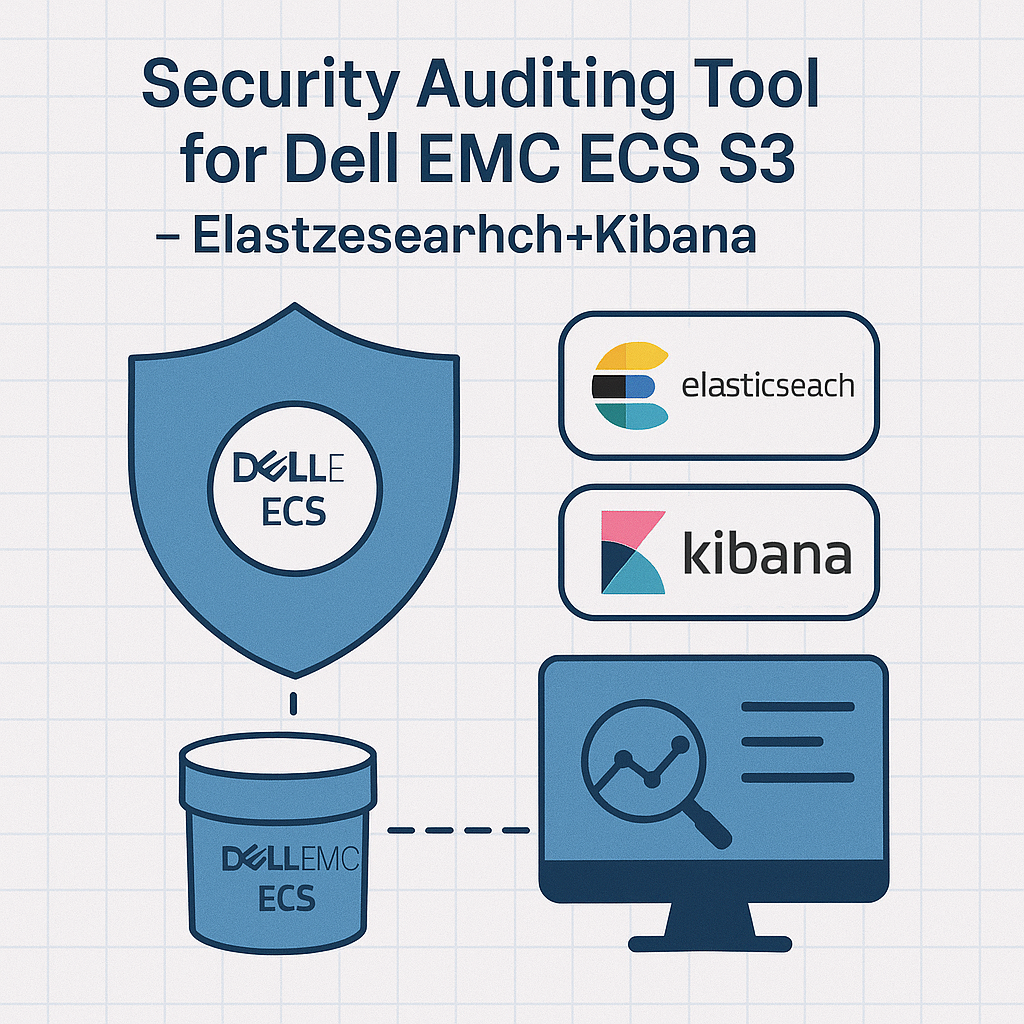
Custom Security Auditing Tool for Dell EMC ECS S3 Buckets Using Elasticsearch + Kibana
Introduction Dell EMC ECS (Elastic Cloud Storage) provides enterprise-grade S3-compatible object storage. However, native auditing and visibility into S3 bucket activity are often limited. To solve this, we developed a custom security auditing tool that collects, parses, and visualizes S3 bucket activity logs from ECS using Elasticsearch and Kibana. The Challenge The Solution ⚙️Data Ingestion Read more